Re-Configure Docker to use Harbor
In part 1, we have generated CA certificates. Using the same CA , we will generate docker client certificates. So , logon to the same harbor host and then go the directory where CA certificates were stored. In our case ;
cd ~/harbor_certs/Generate a CSR for docker and get it signed for the client
$ openssl genrsa -out docker-client.linxlabs.com.key 4096
$ openssl req -sha512 -new \
-subj "/C=IN/ST=Kerala/L=Kollam/O=demo/OU=Personal/CN=docker-client.linxlabs.com" \
-key docker-client.linxlabs.com.key \
-out docker-client.linxlabs.com.csrSign Certificates
$ openssl x509 -req -sha512 -days 3650 \
-extfile v3.ext \
-CA ca.crt -CAkey ca.key -CAcreateserial \
-in docker-client.linxlabs.com.csr \
-out docker-client.linxlabs.com.crtYou will get an output like below.
Signature ok
subject=/C=IN/ST=Kerala/L=Kollam/O=demo/OU=Personal/CN=docker-client.linxlabs.com
Getting CA Private Key
Docker needs the certificate in PEM format , so lets convert the client certificate.
$ openssl x509 -inform PEM -in docker-client.linxlabs.com.crt -out docker-client.linxlabs.com.certOn docker client system , create directories to store certificates.
$ sudo mkdir -p /etc/docker/certs.d/k8s-harbor-registry.linxlabs.comCopy certificate from CA server (harbor host) to the docker client host , then follow below procedure.
$ sudo cp ca.crt docker-client.linxlabs.com.key docker-client.linxlabs.com.cert /etc/docker/certs.d/k8s-harbor-registry.linxlabs.comRestart docker after placing certificates.
$ sudo systemctl restart dockerNow try to logon to the private registry.
If there is no DNS entry for registry FQDN , then make sure the entry is added to /etc/hosts
$ docker login k8s-harbor-registry.linxlabs.com
Username: ansil
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login SucceededVerify docker image pull/push
Download an image from docker hub
$ sudo docker pull alpine
Using default tag: latest
latest: Pulling from library/alpine
aad63a933944: Pull complete
Digest: sha256:b276d875eeed9c7d3f1cfa7edb06b22ed22b14219a7d67c52c56612330348239
Status: Downloaded newer image for alpine:latest
docker.io/library/alpine:latest$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
alpine latest a187dde48cd2 2 weeks ago 5.6MBTag the image for pushing it to private registry
$ docker tag alpine:latest k8s-harbor-registry.linxlabs.com/library/ansil/alpine:latest$ docker push k8s-harbor-registry.linxlabs.com/library/ansil/alpine:latestOutput
The push refers to repository [k8s-harbor-registry.linxlabs.com/library/ansil/alpine]
beee9f30bc1f: Pushed
latest: digest: sha256:cb8a924afdf0229ef7515d9e5b3024e23b3eb03ddbba287f4a19c6ac90b8d221 size: 528
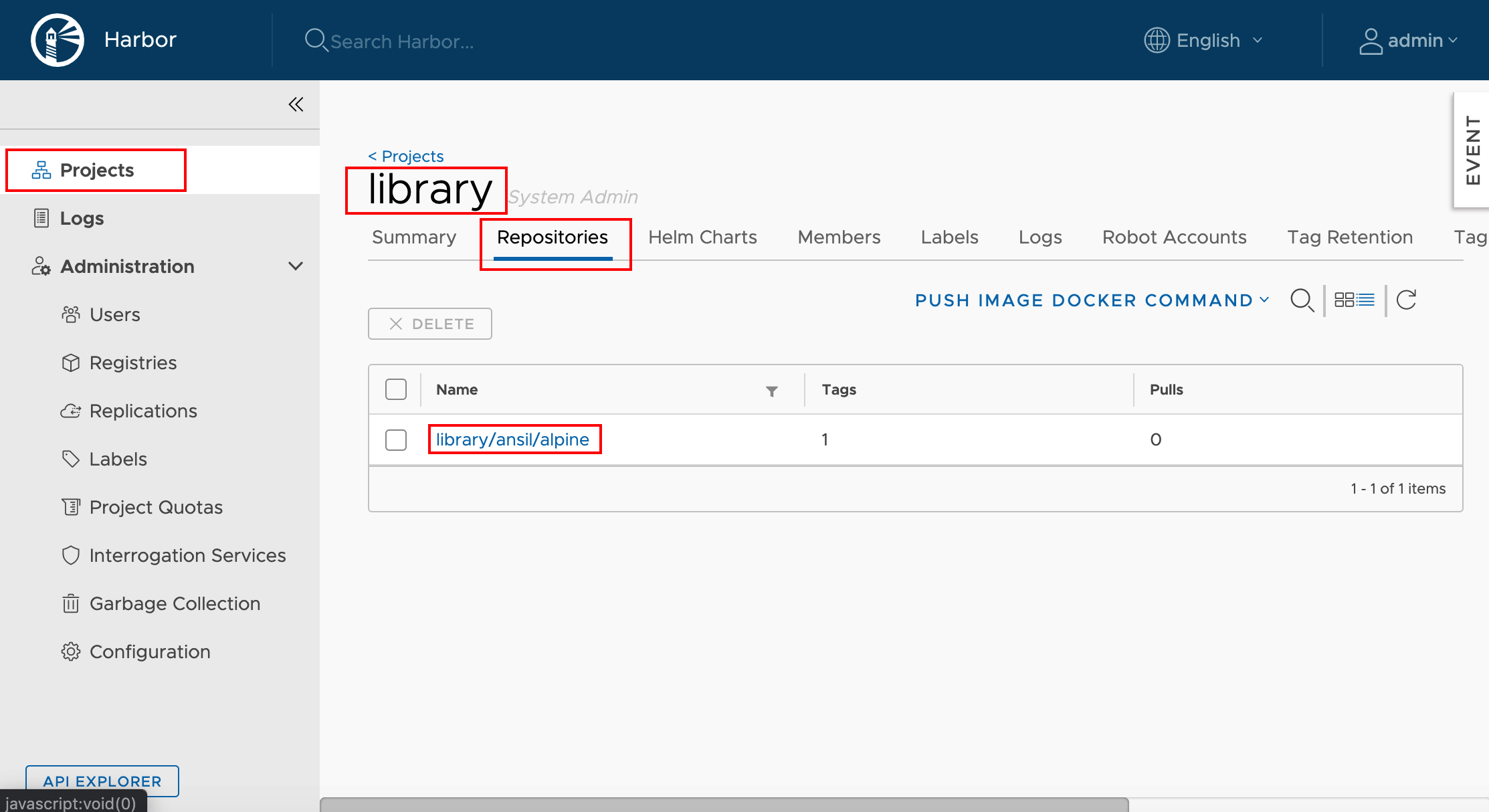
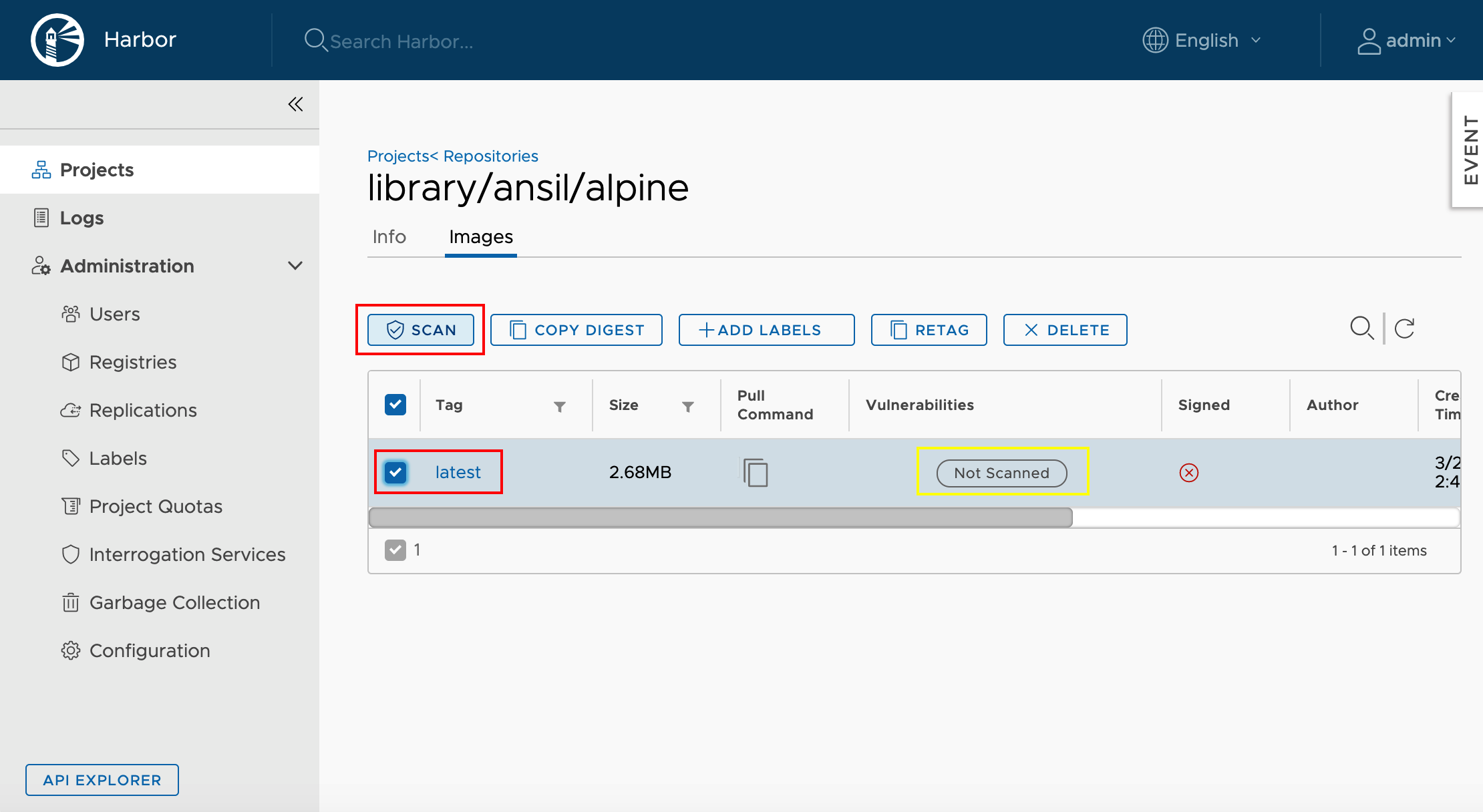
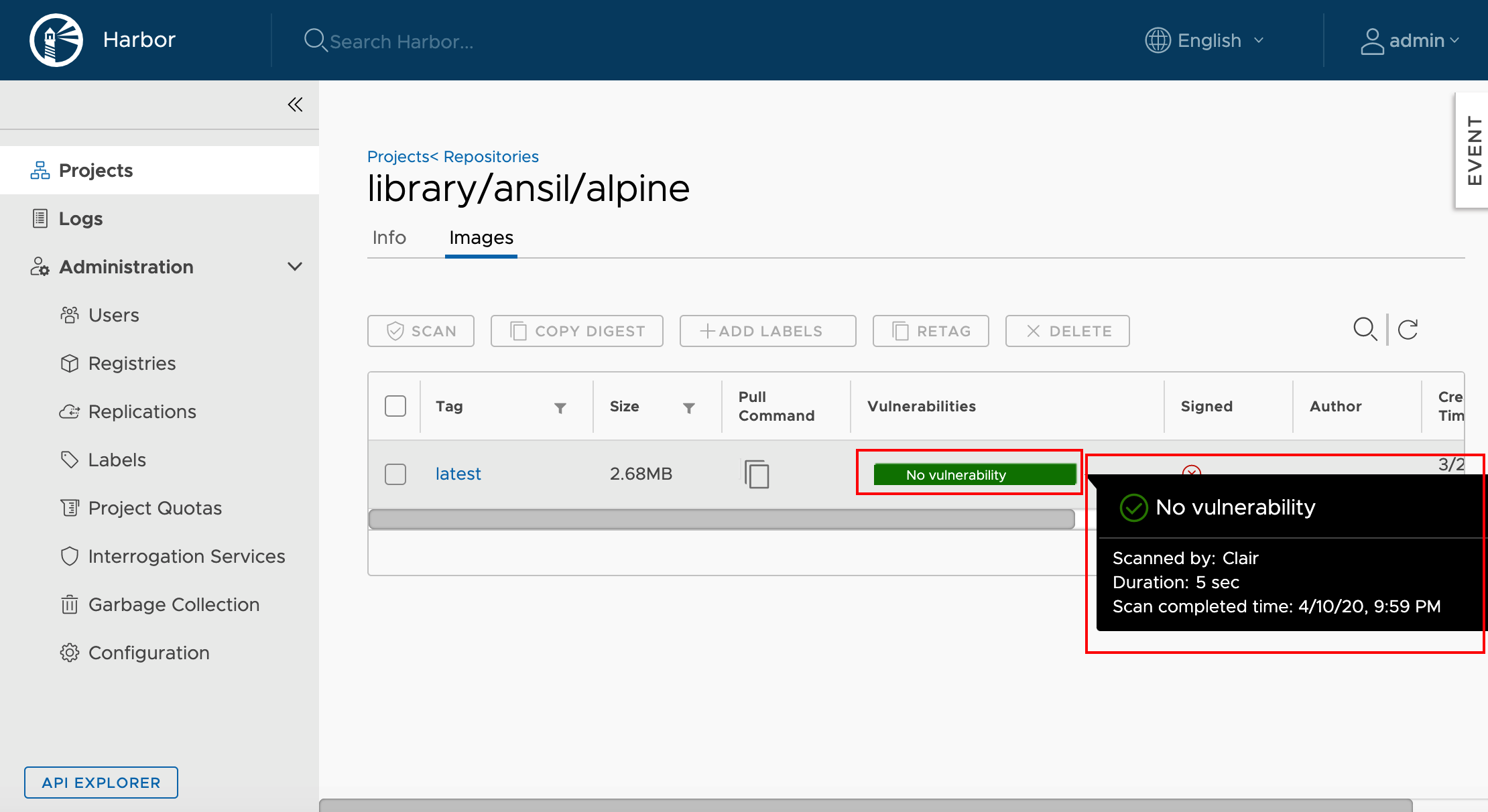
Logon to Harbor UI and verify the status of the new image & scan it for vulnerability